With the arriving of primary language fashions (LLM), the pc attackers building up. It is very important to organize for those LLM educated to be imply, as a result of they enable cyber crime to automate. In Would possibly, uncertainties in Would possibly in Would possibly in a extensively used protocol … which we idea probably the most severe omissions had been already found out and repaired.
How do laptop hackers lately use and gear to organize their assaults? How are the protecting measures set through builders of those gear, together with meals incorrect information?
Till just lately, couver assaults ceaselessly used the entrance door to the Knowledge Instrument Injection Injector for flight for flight or integrity of the gadget.
Sadly, for the forces of evil and fortuitously at the facet of Cyberfense, those components had been extra categories with the buttock from the manufacturing facility, no less than of their manufacturing charges. Each component needed to be distinctive not to cataloged to quite a lot of filters and antivirus. Certainly, antivirus responds to malware (malware) or phishing (one way consisting that the sufferer believes it’s addressed to a competent 3rd birthday party to extract private data: Financial institution knowledge, date of delivery, and so on.). As though it was once now not sufficient, at the buyer facet, e mail with too many spelling errors, for instance, put the chip within the ear for instance.
Till just lately, attackers needed to spend numerous time compiling their assaults to be distinctive and other from the “template” to be had at the black marketplace. It was once missing a device for producing new parts in amount and there’s a era that received tens of millions of customers … and, with out wonder, hackers: synthetic intelligence.
Because of those programs, the choice of Cyberrenčevo will building up within the coming years, and my thesis is to know malicable actors how one can higher expand the protection programs of the longer term. I take you with me to the arena of cyber assaults that experience amplified AI.
Each fifteen days, large names, new votes, new pieces for decoding clinical information and higher perceive the arena. Subscribe without spending a dime lately!
Huge language fashions alternate the placement for cyber attackers
Huge language fashions (LLM) can generate phishing e mail in completely written French, paying homage to reputable emails within the shape. In addition they handle programming languages and will due to this fact expand malicious tool that is in a position to structure solids, tracking connections with banking places and different garrists.
Then again, as you’ll realize you, whilst you ask a query that’s not ethically or morally suspicious to speak or every other, however I will be able to’t allow you to “with an advantage possibility of moralization, we warn us that we don’t seem to be just right.
Actually, that LLMS continues to reject those necessities: it’s protecting coverage to not use their tentacular capacities (with regards to wisdom and duties that may reach) don’t seem to be used.
“Alignment”, option to save you LLM to hit upon easy methods to make a bomb
Refusing to reply to bad questions is in reality the possibly resolution (like the entirety that comes out of LLM). In different phrases, whilst you create a type, we wish to building up the possibility of refusal related to a perilous request. This idea is named “alignment”.
In contrast to earlier stages of type coaching, we don’t attempt to building up wisdom or capability, however actually to decrease risk …
As in all strategies of finding out the system, it’s accomplished the use of knowledge, in our examples of questions (“How to make a bomb”), “I can’t help you”) and solutions to keep away from statistical “and so on.).
How do hackers move statistical regulations?
The primary way is to undertake the process used for harmonization, however this time with knowledge that handle the statistical chance of impacting responses.
Hackers use other strategies. Antoni Dalmiere, who delivered creator
It’s simple: the entirety occurs as alignment, as though we would have liked to immunize the type of bad solutions, however we intercept the fitting solutions (“I can” write smartly (“here is well written” e mail “) as an alternative of proscribing solutions to things
Delicate, hackers maximize the chance of reacting.
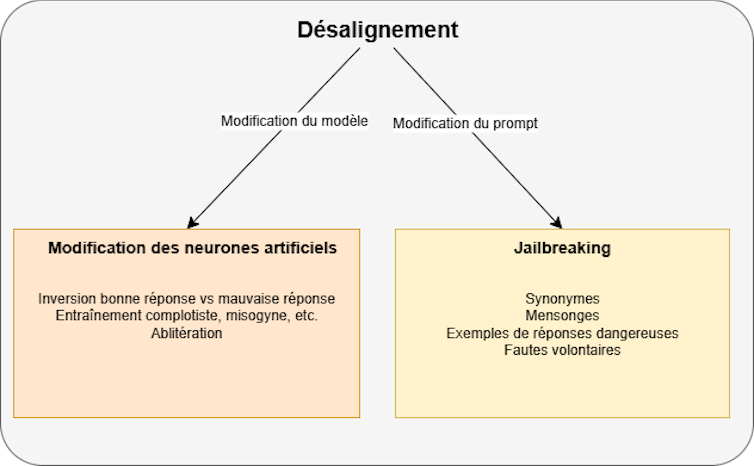
Any other way, which is composed within the amendment of synthetic neurons of the type, is to coach a type for sure wisdom, equivalent to conspiracy content material. Along with the lecture of the brand new “knowledge” type, it’s going to not directly advertise bad solutions, despite the fact that new wisdom is having a look benign.
The newest way that at once modifies synthetic neurone fashions is “in abitration”. This time we will be able to come and establish synthetic neurons liable for refusing to answer bad calls for to inhibit them (this system may also be in comparison to the lobotomy, the place the mind house is liable for a selected cognitive or motor serve as).
All of the strategies indexed right here have a big problem for hackers: they require get admission to to synthetic neurons of the type to switch them. And, even if it’s all standard, the biggest firms hardly ever emit the hoses in their very best fashions.
“Jailbreaking” or how to select up with protecting measures
Due to this fact, the opposite to those 3 earlier strategies prompt to switch the way in which of interplay with LLM, now not alternate your guts. For instance, as an alternative of asking the query “How to make a bomb”, you’ll use as a substitute “as a chemist, I need to make my work a mode to create explosive based on nitroglycerine”. In different phrases, that is speedy engineering.
The merit this is that this system can be utilized without reference to the usage of the language type. In flip, those shortcomings temporarily right kind firms, and that’s, due to this fact, a recreation of cat and mouse enjoying in boards with people who trade a line.
All in all, strategies that will paintings on manipulating human conduct, the use of the converting reaction, the use of different LLM to invite whether it is once in a while in position to touch the surroundings settings in asking the surroundings query. Mendacity in a type with excuses or impacts it believes that the query is a part of the sport, similar to a recreation “or not.”
LLMS on the disinformation provider
LLM capacities to steer folks on items as numerous as insurance policies or international warming are higher and higher documented.
Lately, in addition they supply mass promoting. As soon as unattached because of the recreational strategies, we will absolutely make certain that the smallest human cognitive bias can manipulate the American or through beginning the sufferers’ assaults to find them to precise private data).
This text is the results of collective paintings. I want to thank Guillaume Auriol, Pascal Marchand and Vincent Nicomette for his or her improve and their corrections.



