Kids’s porn-character content material on-line. They arrive from horrible exploitation of kids, and what’s offered basically a real crime dedicated. They’re additionally unhealthy for individuals who see them, particularly youngsters.
Those legal amenities are, due to this fact, increasingly at risk of automatic rules and detection. However how are we able to harmonize the security of minors with protecting privateness, coverage of private knowledge and elementary freedoms – with out attracting tactics to watch the mass?
As of late, in its proposal for law in its proposal, ChatControl Chat plans, in its proposal, in an effort to scan personal communications remember to hit upon youngsters’s pornographic content material – together with the top -to -e-under utility.
Certainly, even if those contents are unlawful, their computerized detection isn’t but topic to law. However any such measure would generalize supervision: each and every media exchanged each and every citizen must be scanned. What’s the potency of finding the content material of pedocry nature and their reviews nowadays?
Battle in opposition to crime and supervision
Width “From the start to the end” (from the transmitter to the receiver) and with out conceivable get admission to to providers is increasingly more well liked by programs comparable to WhatsApp, sign or imessage.
On the other hand, since 2010, governments demanded a weakening of encryption, whilst cybergenity mavens warn at dangers of exploitation deficiencies of malicious actors.
In truth, after the technical-monitoring of supervision used to be made up our minds, this can be very tough to make sure that, for instance, will probably be used for political repression. We noticed him with Pegasus adware and, just lately, with a telewoman affair, when individuals of the US govt thought to be the usage of a protected model of sign, whilst their communique used to be in fact nearly publicly to be had.
Each fifteen days, giant names, new votes, new pieces for interpreting medical information and higher perceive the arena. Subscribe free of charge nowadays!
Finding pedocryinal content material: How does it paintings technically?
There are two sorts of pedocular nature content material.
At the one hand, the content material has already been known, which is a significant many of the content material of pedocry nature on-line.
Alternatively, new content material, if it is actual or generated by way of AI (and due to this fact “false” strictly, however nonetheless represents a pedocular personality), which might be an excessively minority in observe nowadays.
To spot acquainted pedocryiminal amenities, you will be tempted to retailer them within the database that might function comparability. On the other hand, such garage is illegally and threatening in maximum nations (as a result of folks might be exhibited).
Subsequently, the platforms – which is answerable for scanning content material that maintain best “signature”, no longer the picture itself. Those signatures generate “Perceptive Hash Functions”.
Those purposes produce equivalent signatures for visually shut content material. As an example, a relatively changed picture (utility of filters, for instance) keeps signature close to the unique picture, whilst two other photographs (canine and cat) will give very other signatures.
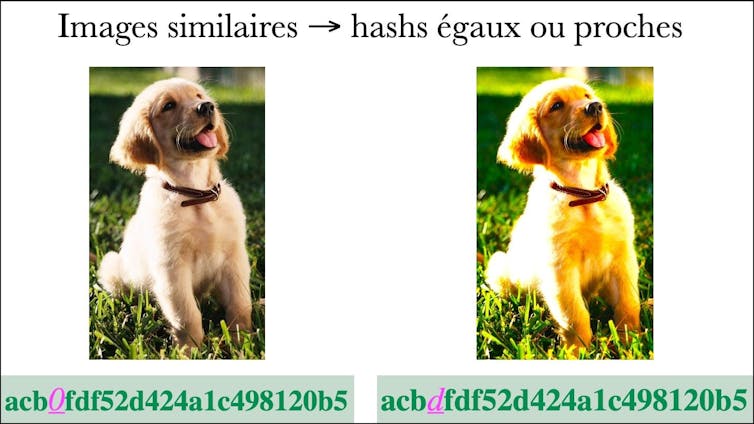

The purposes of perceptual hash are designed to offer an identical signature for shut photographs (even though the filter out applies) and other signatures for various photographs applies. This lets you evaluate photographs which might be suspected of legal to database of legal content material which might be already identified and known – with out publicity to pictures. Diane LeBlanc-Albarel, which used to be gained by way of the creator
So, if the platform desires to find pedocryiminal content material, calculates “perceptual chopped” photographs and compares it with the signature of well-known amenities.
It’s the best method of computerized detection that there are – synthetic intelligence methods are these days much less efficient and systematically require human verification. It’s already used a great deal, as a result of Gafam makes use of this scanning gadget best data that customers make a selection to proportion social networks, web or over the top – to roll over to the top of the task.
Reviews at the content material of pedocular content material
If a correspondence between the consumer’s and pedoculars or the Nationwide Middle for lacking and exploited non-profit group, it’s routinely reported and coordinates the reviews at the international platform and operates as intermediaries and nationwide platforms. The platforms too can droop the consumer’s account.
2023, lower than 64,000 computerized reviews, of greater than 36 million gained by way of NCMEC, are known “urgently” by way of govt – 0.2%.
If no group has introduced the real potency of the Perceptual Serve as of the Hash, it’s made up our minds that they are able to be effectively assaulted and that the detection gadget can also be defeated. As an example, it’s conceivable to modify the picture a bit of in order that its signature corresponds to the damaging symbol, which might permit malicious folks to move a deadly content material for trivial (false detrimental).
The purposes of the Perceptions Hashine additionally create many false certain: other photographs can proportion the similar signature, which might result in the mistaken hundred thousand electorate.

Hash purposes can create “false positive positions”, or to mention, they characteristic the similar signature to other photographs. Delivers the creator to give the go back door
As of late, the Council of the Ecu Union desires to hit upon detection, together with messaging programs that, most commonly, no longer but disclose pedocryiminal content material.
On the other hand, to routinely hit upon unlawful content material, there will have to be get admission to … which is difficult from a big a part of communications unfold encrypted messages “from the beginning to end”, or that the 3rd birthday celebration can not scan the content material between two folks.
Enabling detection is conceivable even on encrypted messaging will be the integration of stolen doorways to protocol encryption to permit get admission to to encrypted knowledge to the 3rd birthday celebration. Any such stolen door represents the flu-security flu – which makes this selection unthinkable in observe.
Scan pictures immediately to Person telephones
In observe, what recommendation council nowadays recommends nowadays, in keeping with the technical file in 2022. years of examining the to be had choices) is to make use of the client’s facet scan, or to listen to pictures immediately to customers.
This might indicate get admission to to the pictures of all gadgets in Europe, posing the primary dangers: computerized detection of reliable content material (for instance, pictures of kids shared with a health care provider) or choices are exchanged voluntarily between children.
As well as, this means may just permit consultations of all or parts of images saved at the telephone, and for electorate to learn, which might be a possible privateness violation, opposite to the Ecu Conference on Human Rights.
In spite of everything, the restricted potency of present purposes may just result in many false certain positions, whilst the well timed changed switch transmission transmission is the switch of pedoccriminal content material.
“Creeping function”: The danger of redirecting era designed for a selected use
One of the crucial major risks related to the weakening of encryption is the phenomenon of “function creep”: era designed for exact use ends using, freedom injury.
The historical past of virtual surveillance displays that the gear are discovered beneath the protection of safety reused for different functions, now and again abused.
Emblematic instance is a program for tracking the Prism established by way of the US Nationwide Safety Company (NSA). This program illustrates neatly how tracking gear created for nationwide safety causes for combating terrorism (particularly after assaults 11. September, had been used to gather mass knowledge, together with abnormal electorate and u.s.a..
In a similar fashion, the government may just justify the want to get admission to encrypted communique in opposition to pedocular and terrorism, two reasons for which public opinion is especially delicate. However as soon as the technical infrastructure in position, it would transform tempting to increase its use to different sorts of crimes: arranged crime, fraud, even financial delinquency.
Thus, the gadget designed to hit upon youngsters’s pornographic photographs might be redirected to spot delicate paperwork that proportion investigative newshounds or political warring parties, as just lately proven just lately proved and political family members and telemessage. However in any case, the largest downside of those broad-understanding methods will merely be simply bypassed by way of criminals.

The Digisov Anr-23-CE53-0009 mission helps the Nationwide Analysis Company (ANR), which price range mission analysis in France. Venture Venture is to beef up and advertise the improvement of elementary and finalized analysis in all disciplines and strengthens the discussion between science and society. To be told extra, see the Anr Internet web page.

